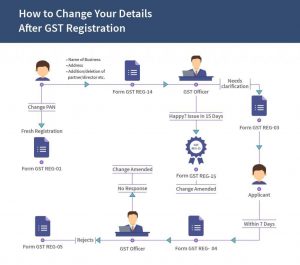
What is non control data?
What is non control data?
Most memory corruption attacks and Internet worms follow a familiar pattern known as the control-data attack. Non-control-data attacks corrupt a variety of application data including user identity data, configuration data, user input data, and decision-making data.
What is data only attack?
Data-only attacks target the program’s data rather than its control flow. Our threat model consists of a binary with a known memory cor- ruption vulnerability that is protected with the state-of-the-art control-flow hijack mitigations, such as CFI along with a Shadow Stack.
Which is the most common threat to databases?
“In both types, a successful input injection attack can give an attacker unrestricted access to an entire database.” *Malware. A perennial threat, malware is used to steal sensitive data via legitimate users using infected devices. *Storage media exposure. Backup storage media is often completely unprotected from attack, Gerhart said.
Who is responsible for the destruction of the Amazon rainforest?
However, livestock can still be indirectly responsible for rainforest destruction since intensively farmed animals in the UK are fed a high protein plant called soya. China, with its growing demands for beef has in recent years become the largest consumer of soya from Brazil.
How does the destruction of the rain forest affect the world?
The destruction of the rainforest could affect the world’s climate. During the day, the rainforests absorb huge amounts of carbon dioxide from the air to make food in a process called photosynthesis. A by-product of photosynthesis is oxygen. Tropical rainforests absorb about 20% of the world’s man-made carbon dioxide emissions.
How big is the deforestation of the Amazon rainforest?
The disappearance of the forest is called deforestation. As populations have grown and demands for land and timber have grown greater, so the deforestation has accelerated. Current rates of deforestation amount to about 6 million hectares a year.